
Catch me if you happen to can
“There is no such thing as a know-how at this time that can’t be defeated by social engineering.” —Frank Abagnale
On the 2018 Gartner summit, I had an opportunity to take a seat within the entrance row for the keynote speech given by Frank Abagnale. Catch Me If You Can, the critically acclaimed movie starring Leonardo de Caprio and Tom Hanks (2002), is predicated on Abagnale’s exploits as a con artist that led to his widespread notoriety.
After serving time in jail for impersonating a health care provider and a lawyer along with his escapades as a pilot, Abagnale went on to work for the U.S. Federal Bureau of Investigation (FBI), the place he began out investigating individuals who cast checks, counterfeited paperwork, and embezzled cash. Whereas he spent a complete of 43 years with the FBI, he handled nothing however cybercrime for the final 20 years of his profession. Abagnale labored on each knowledge breach, together with TJX (the dad or mum firm of TJ Maxx, Marshalls, and Dwelling Items, amongst others) in 2007, and, extra lately, Marriott and Fb.
Throughout his keynote tackle on the Gartner convention, Abagnale recalled how, on the age of 16, he used social engineering to impersonate a pilot and referred to as Pan Am’s company headquarters to acquire a uniform by means of the buying division.
In response to Pan Am’s estimates, between the ages of 16 and 18 Abagnale flew as a “deadhead” passenger (which means he didn’t take the controls of the airplane) on greater than 250 flights and traveled a couple of million miles to 26 international locations, all on their dime.
From bodily to digital, from landline to e mail
Fifty years in the past, the landline cellphone was the one device Abagnale needed to rip-off an organization by speaking his method in. At present, the “assault floor space” has modified drastically due to the web, textual content messages, emails, social media, and extra.
Cyber threats maintain evolving and getting smarter, which makes it extra essential than ever to maintain a watch out for them.
A latest report from IBM states that in 2020, the typical value of a cyberattack on a enterprise was $3.86 million, and it took greater than 200 days to discover a breach.
Any enterprise, massive or small, in any business generally is a sufferer of cybercrime. One factor all of them have in widespread, although, is that they’re prone to occur due to human error.
“The one factor that I’ve learnt is that each breach happens as a result of anyone in that firm did one thing that they weren’t purported to do, or anyone in that firm didn’t do one thing they had been purported to do,” Abagnale mentioned.
Social engineering assaults are one of the pervasive and harmful types of cybercrime that corporations face at this time, and phishing is essentially the most prevalent type of social engineering.
What’s phishing?
Social engineering is an umbrella time period for makes an attempt to mislead or deceive web customers. Phishing is the most well-liked type of social engineering.
Phishing is the follow of sending deceptive messages, sometimes by e mail, that seem to come back from a reliable supply. In reality, World Phish Report states that 1 in each 99 mails is a phishing assault. Phishing emails deceive customers into putting in a bug, clicking on a malicious hyperlink, or divulging private data, equivalent to bank card particulars and login credentials.
Social engineering assaults, equivalent to phishing, are often accompanied by different threats, equivalent to malware, code injection, and community assaults.
In response to Verizon’s 2021 Knowledge Breach Investigations Experiences, round 25% of all knowledge breaches embody phishing, and 85% contain human error.
Forms of phishing assaults
ScammingScams are sometimes distributed by unsolicited e mail. They’re meant to deceive victims into divulging data that may lead to identification theft or fraud. Cybercriminals use scams to cheat individuals out of cash or steal their identities by getting them to surrender private data. Scams embody pretend job advertisements, funding alternatives, notices of inheritance, lottery prizes, and transfers of funds. Scammers usually attempt to make cash off tragedies like hurricanes, the COVID-19 disaster, and different tragedies. Rip-off artists make the most of individuals’s kindness, worry, or sympathy. In the course of the peak of the Covid-19 outbreak, phishing incidents elevated by 220% in comparison with the yearly common. |
Spear phishingSpear phishing is a extremely tailor-made rip-off. Cybercriminals conduct in depth analysis on their targets—which may be people, organizations, or companies—and produce rigorously crafted mail, often impersonating a trusted colleague, web site, or enterprise. Usually, spear-phishing emails try and receive delicate knowledge, equivalent to login passwords or monetary data, which is subsequently used to perpetrate fraud, identification theft, and different crimes. Greater than 71% of focused assaults make use of spear phishing. Though spear phishing is usually meant to steal credentials and take over accounts, the cybercriminals may additionally infect victims’ computer systems and networks with malware, resulting in monetary loss and injury to their popularity. Whaling is a type of spear phishing that targets public personalities, executives, and different giant targets, therefore the moniker. Extortion scams: This type of spear-phishing is changing into extra refined as a result of it bypasses e mail gateways. Cyber criminals exploit stolen usernames and passwords to extort cash from victims by pretending to have an incriminating video on the sufferer’s laptop and threatening to share it until they pay. Extortion scams are under-reported as a result of they’re embarrassing and delicate. |
Enterprise e mail compromise (BEC)BEC scams are one other type of spear phishing. Malicious customers compromise enterprise e mail accounts to commit fraud and different crimes. They obtain this by means of social engineering, hacking, and spoofing. Three variants of BEC frauds are: The fraudulent bill rip-off includes impersonating a well known group. The goal receives a cost request from this group. CEO fraud includes hijacking an government’s e mail tackle and sending fraudulent emails to workers dealing with monetary requests. Messages from compromised accounts are despatched to organizations or contacts the consumer is aware of. These comprise different organizations’ payments and cost requests. Payroll scams, tax threats, travel-based scams, and pretend charities are a few of examples of BEC scams. |
Electronic mail spoofing/ impersonationAn impersonation assault happens when fraudsters seem as a trusted contact that coerces workers into sending funds or disclosing crucial data. URL phishing or area impersonation is a kind of assault the place cyber criminals use emails to trick individuals into getting into private data on a pretend web site that appears actual. Following are the other ways cybercriminals exploit URLs:
Clone phishing employs a beforehand delivered or legitimate e mail with attachments or hyperlinks. The clone is a virtually similar copy of the unique, with the attachments and hyperlinks changed by malware or a virus. Dialog hijackings are extremely personalised domain-impersonation assaults wherein cybercriminals insert themselves into current enterprise discussions or create new ones to steal cash or private data. |
Model impersonationThe aim of name impersonation is to deceive individuals into divulging private or in any other case delicate data by impersonating a agency or a model. Service impersonation is a type of phishing assault that impersonates a well known company or in style enterprise utility. It’s a standard phishing assault on some extent of entry to reap credentials and conduct account takeover. Moreover, service impersonation assaults are used to gather personally identifiable data (PII), equivalent to bank card and Social Safety numbers. Microsoft is most frequently impersonated. Credentials for Microsoft and Workplace 365 are very precious as a result of they let hackers get into organizations and launch extra assaults. The most typical Workplace 365 phishing assaults are e mail non-delivery, reactivation requests, and storage limitation alerts. Model hijacking happens when an attacker seems to make use of the area of a agency to impersonate the corporate or one in all its staff. That is sometimes achieved by sending emails with pretend, or spoofed, domains that look to be legitimate. Abysmal DMARC adoption is making it simpler for scammers to spoof manufacturers. (77% of Fortune 500 corporations should not have DMARC insurance policies arrange.) |
Lateral phishingA lateral phishing assault sends emails from a official however hacked account to unwary recipients, equivalent to firm contacts and exterior companions. Attackers can goal a variety of individuals and organizations after buying entry to an organization’s e mail account. In a latest spear-phishing report that analyzed lateral phishing assaults carried out in opposition to almost 100 organizations, 63% of assaults employed “shared doc” and “account drawback” messages (e.g., “You have got a brand new shared doc”). One other 30% of occasions used refined communications, focusing on enterprise corporations (e.g., “Up to date work schedule,” “Please distribute to your groups”) In essentially the most refined assaults, 7% used organization-specific content material. |
Organizational practices equivalent to distant and hybrid work cultures, BYOD (carry your personal machine) and even carry your personal SaaS have blurred the limitations between the non-public {and professional} surroundings. Each employers and workers should safe their units and digital area at each house and on the office.
Phishing crimson flags
There are a number of crimson flags that workers should pay attention to to determine potential phishing scams earlier than they will hurt a person or a enterprise.
Inconsistent net addressesSearch for e mail addresses, hyperlinks, and domains that don’t match. It’s a good suggestion, for instance, to look at a earlier correspondence that matches the sender’s e mail tackle. Earlier than clicking on a hyperlink in an e mail, recipients ought to at all times hover over it to view its vacation spot. If the e-mail seems to be from Acme, however the area of the e-mail tackle doesn’t comprise “Acme.com,” it’s probably phishing. |
Unsolicited attachmentsMalware is often disseminated through phishing emails with odd attachments. In case you obtain an “bill” within the type of a .zip file, an executable, or the rest out of the peculiar, it’s probably malware. In response to a latest Menace Report from ESET, these are the commonest sorts of dangerous recordsdata hooked up to phishing emails:
|
Inconsistent hyperlinks and URLsDouble confirm URLs. If the hyperlink within the textual content and the URL displayed when the cursor lingers over the hyperlink aren’t comparable, you’ll be directed to an undesirable web site. If the URL of a hyperlink doesn’t seem like appropriate or doesn’t match the context of the e-mail, you shouldn’t belief it. Take the added safety measure by hovering your mouse over embedded hyperlinks (with out clicking!) and making certain that the hyperlink begins with https://. Don’t open the hyperlink if the e-mail is sudden. As a precaution, go to the web site you imagine to be the origin of the e-mail straight. |
Generic salutationIf a company with which you do enterprise needed account data, the e-mail would name you by title and certain direct you to name them. Phishing emails often comprise generic greetings equivalent to “Expensive valued member,” “Expensive account holder,” and “Expensive shopper.” |
Tone and grammar errorsThe tone and grammar of an e mail from a official firm needs to be impeccable. A phishing e mail will often comprise misspellings and grammar errors. If an e mail appears out of character for its sender, it’s probably malicious. There’s a function behind improper syntax. Hackers give attention to the much less tech-savvy as a result of they imagine they’re much less vigilant and, subsequently, simpler targets. |
Uncommon requestsIf an e mail asks you to do one thing out of the peculiar, it could possibly be an indication that it’s malicious. For instance, if an e mail says it’s from a sure IT staff and asks you to put in software program, however these duties are often dealt with by the IT division as a complete, the e-mail might be malicious. In response to analysis by KnowBe4, these had been the commonest topic traces for real-life phishing emails in 2021:
Faux LinkedIn messages are utilized in 47% of social media phishing makes an attempt. Individuals usually get contextual emails asking them to reset their passwords or giving them “data” about attainable new connections (“You confirmed up in new searches this week!” “Persons are your LinkedIn profile!”). |
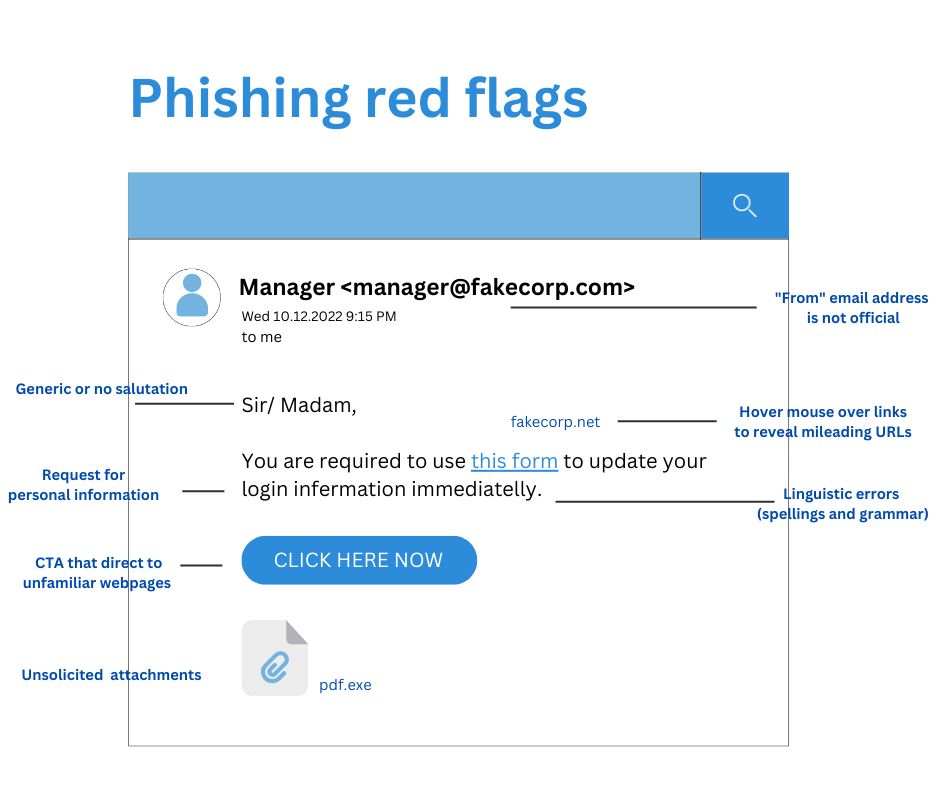
Indicators of phishing
The position of enterprises in e mail safety
All e mail suppliers have built-in virus and phishing prevention. Signature-based antivirus controls cease recognized malware threats. In addition they block unsolicited bulk mail and guard in opposition to common phishing emails.
Cybercriminals’ assaults are getting more and more refined. With phishing and cloud e mail migration, corporations want superior menace safety to defend delicate knowledge from attackers.
The superior e mail safety contains a variety of capabilities and options. Let’s have a look at a number of the key e mail safety options and the way they work.
Safe e mail gateway (SEG)Utilizing a SEG is essentially the most frequent methodology for shielding e mail. SEGs are sometimes configured as a cloud service. Gateway options depend on exact insurance policies that seek for widespread fraudulent key phrases in an e mail. Gateways implement URL filtering and URL rewriting applied sciences to stop entry to dangerous web site hyperlinks supplied over e mail, together with all recognized malware and phishing websites. |
SandboxingSandboxing is a complicated method that’s appropriate with SEG out of the field. Earlier than being delivered to customers’ inboxes, suspicious recordsdata and hyperlinks are screened for safety in an remoted check surroundings. Based mostly on a sandbox evaluation, new malware signatures may be developed to thwart future assaults. |
Electronic mail knowledge safety (EDP)EDP options incorporate encryption to trace and forestall unlawful entry to e mail content material earlier than or after it’s transmitted. EDP may assist stop inadvertent knowledge loss owing to misdirected receivers. The know-how scans all outgoing e mail for predefined patterns that will point out the presence of delicate materials, equivalent to bank card numbers, Social Safety numbers, and HIPAA medical phrases. By default, messages containing such delicate data are encrypted. |
DMARC, DKIM, and SPFOrganizations make use of DMARC, DKIM, and SPF as e mail authentication methods to stop area spoofing and model hijacking. DMARC reporting reveals how an e mail area is utilized, enabling a company to implement DMARC enforcement insurance policies that stop spoofing of the area. A SEG should assist the protocols talked about above. |
Built-in cloud e mail safety (ICES)ICES options use API entry to the cloud e mail supplier to investigate e mail content material with out modifying the mail change (MX) file. API-based inboxes make the most of entry to earlier e mail communication knowledge to assemble a communication identification graph, which is a statistical mannequin distinctive to every group’s consumer. The identification graph is then used to determine communication patterns that don’t correspond to the statistical mannequin. This allows the prediction and prevention of spear-phishing assaults that bypass the gateway. |
Zoho participates in Cybersecurity Consciousness Month
“Hackers don’t trigger breaches, individuals do.” —Frank Abagnale
Each October is Cybersecurity Consciousness Month. The aim of this annual world marketing campaign is to teach and empower the general public to guard their knowledge and privateness on-line by growing their information of the most effective practices for staying safe.
This yr, Zoho Company is happy to announce its participation on this yr’s marketing campaign. Learn our weblog on how each of the corporate’s divisions, Zoho (software program for companies) and ManageEngine (software program for IT administration and safety), together with our workers, clients, and companions, are contributing globally to considerably improve cybersecurity on-line each at work, and at house.
Conclusion
Phishing and comparable scams won’t disappear quickly. The best solution to shield your self and your online business is to implement safety measures that delay somebody’s means to focus on key personnel.
Whether or not you select digital signatures, code phrases, encrypted communications, or an in-house resolution, be certain that your customers know the dangers. They have to know why that is essential and what to do to guard themselves, their workplaces, and their private data.

